
Asking “how secure is Control Web Panel (CWP)?” is important when considering a web hosting panel.
It’s easy to simply say CWP is pretty secure for up to small and medium-sized businesses. But the best answer is that it depends on whether you:
- Use the latest, best security practices
- Understand your cyber attack surface, and
- Properly audit security logs for better ways to harden your environment
It’s even more relevant when you realize that CWP, even when it was known as “CentOS Web Panel,” isn’t nearly as popular as Plesk and other proprietary Linux control panels.
Below we’ll discuss important items to consider when regarding how secure CWP server hosting truly can be.
Common Security Concerns To Consider
CWP has a free and premium version – CWPpro.
We’ve known for years that “free” sometimes comes with strings attached. Remember the decades-old saying:
“If you’re not paying for the product, you are the product.”
That can come in the form of software collecting your usage data to learn how to improve their product or, in the worst case scenario, it’s spyware or other malicious software you don’t want.
However, sometimes “free” truly means there is no charge. This describes CWP. Experienced system administrators have the skills to manage a web server with only Secure Shell (SSH) – the terminal. But busy or junior sysadmins may prefer a web interface for greater ease of use, especially if granting other users access to manage their own data.
CWP is developed so essential system tasks can be completed securely by authorized users after dependable authentication measures. Therefore, you can disable shell access and more easily determine what each user can do in the dashboard.
Reviewing CWP’s Security Vulnerability Reports
Popularity of certain software tends to create more attention from cyber criminals as the potential for gains in stolen data increase. Think of how often you hear of Windows viruses versus in FreeBSD. However, CWP doesn’t seem to be targeted often judging by the National Vulnerability Database (NVD).
The latest CWP Common Vulnerabilities and Exposures (CVEs) were reported on January 22, 2022 (three months before the release of this blog) by The Hacker News. An unsecured API key vulnerability (CVE-2021-45466) and file inclusion vulnerability (CVE-2021-45467) could reportedly be used for remote code execution (RCE) attacks. Fortunately, this is just a proof-of-concept, meaning that this was done as an experiment. There are no public reports of these exploits being used in the wild. The initial report itself even states that it isn’t easy to execute and doesn’t expose much data.
Still, CWP released three security updates within two weeks of the report, according to their changelog. That’s a good indication that CWP developers pay attention to security bug reports and are serious about cybersecurity.
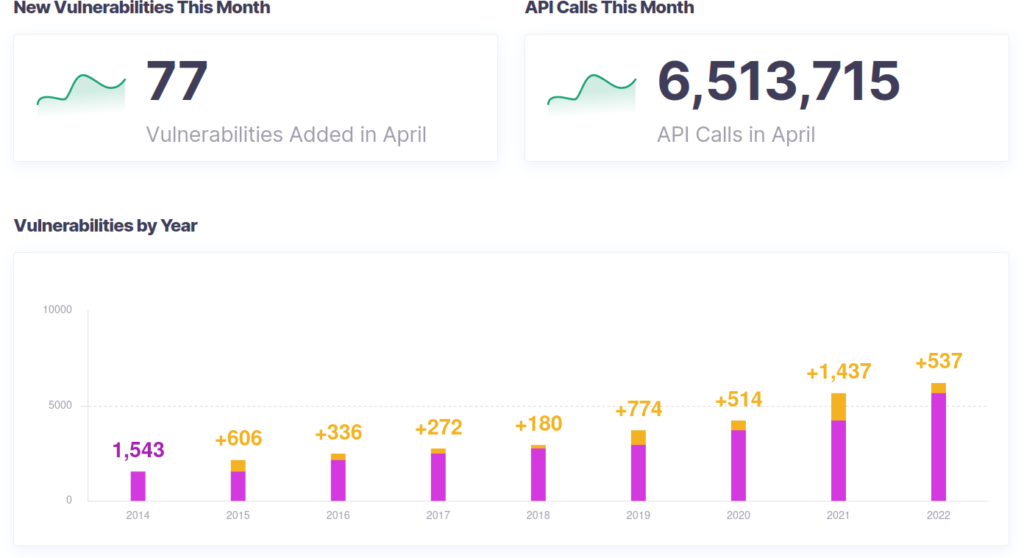
Shodan reportedly told SecurityWeek that there’s been a gradual increase in CWP installations throughout recent years. So there may soon be a point where cyber attackers directly target CWP. But that seems years away as of now.
For some context, there are seven WordPress core CVEs from this year according to WPscan.com.
Is CWP Up-to-Date With Security standards?
The latest server security protocols CWP should assist with implementing are DNS security extensions (DNSSEC), HTTP/3, and common TXT records.
As of now, DNSSEC on CWP servers must be configured manually with raw BIND DNS files. So it is possible to do, but CWP won’t be of any help for the task as of now.
HTTP/3, as does HTTP/2, depends on web server software support before a control panel can create a button to enable it. Apache, the most popular web server, doesn’t support HTTP/3 yet. But it takes less than five minutes to enable HTTP/2 with NGINX in CWP and there is support for LiteSpeed.
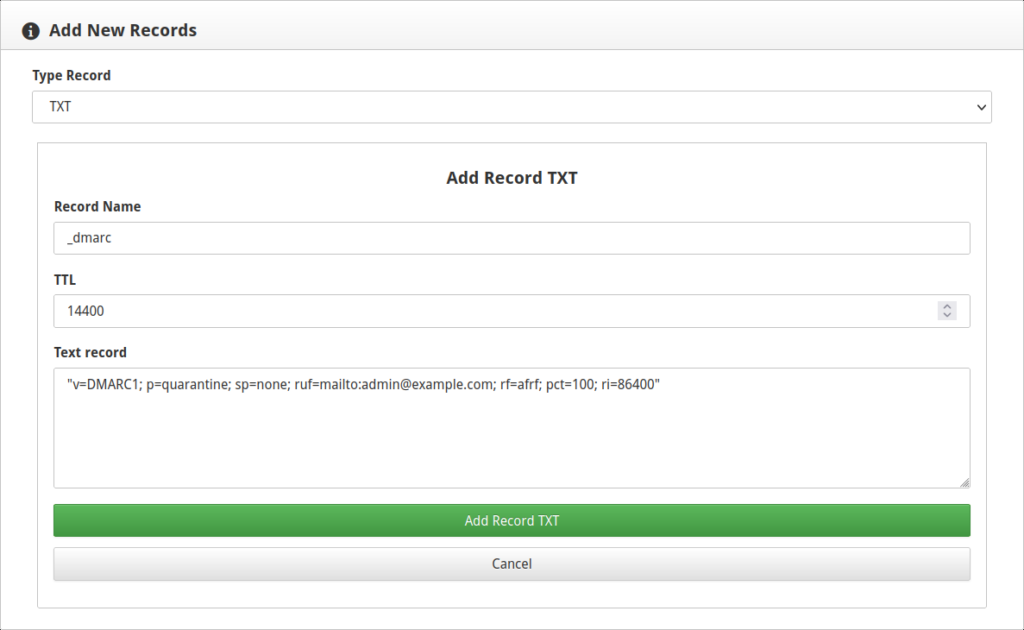
However, one important feature set missing from CWP is a wizard for creating the most common TXT records:
- DomainKeys Identified Mail (DKIM)
- Sender Policy Framework (SPF)
- Domain-based Message Authentication Reporting and Conformance (DMARC)
There are no drop-down menus to help you choose between allowed tags or realize any mistakes. It’s just a large textbox. You must use other means to ensure you’ve written DNS records correctly and secure enough to suit your requirements.
For example, take Brand Indicators for Message Identification (BIMI), which is basically a TXT record linking to a special version of your logo. When you send an email, the receiving email provider checks your DKIM, SPF, and DMARC records. If they match the header info of your email, the BIMI DNS record will push your BIMI logo to show beside your email address in supporting email hosting providers. This indicates the email is legitimate to help mitigate business email compromise (BEC) attacks.
Cool, right? Well, the challenge is that when learning how to create BIMI records in CWP you’ll need to check that your DKIM, SPF, and DMARC records are also correct. Not to mention learning how to create a proper Tiny SVG format of your logo.
CWP Server Hardening Capabilities
CWP meets the basics for expected security tools that authenticate users trying to access the application. The User Login Security page allows you to limit the amount of failed login attempts. CWP also allows you to:
- Create SSL certificates with AutoSSL
- Protect against brute force login attacks
- Create and schedule backups
- Limit processes for a user
- Toggle Secure Shell (SSH) access
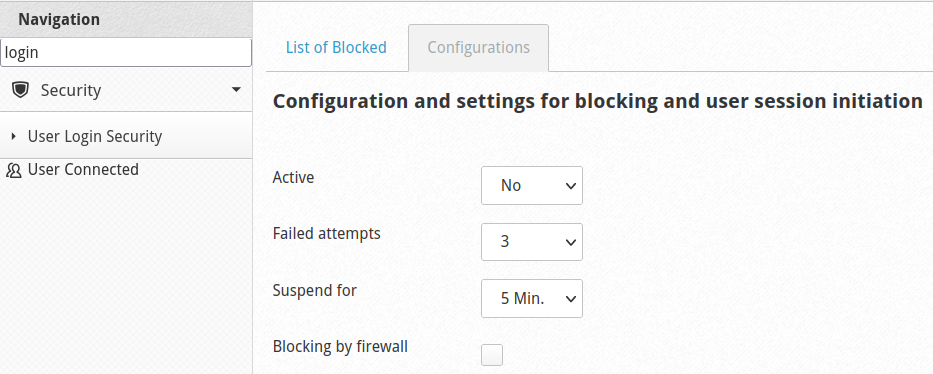
CWP does not have a two-factor authentication (TFA) feature at this time.
Mostly everything else security related must be handled outside of native CWP features, from the CWP terminal emulator or SSH, or with third party software.
CWP Server Security Plugins
CWP makes it easy to install the necessary anti-malware plugins to suit the average user’s needs for Linux malware protection:
- Maldet + ClamAV malware scanner
- Rkhunter rootkit scanner
- ConfigServer Security & Firewall (CSF)
- Lynis system security auditor
- Symlink scanner
- ModSecurity web application firewall (WAF)
- PHP Defender with Snuffleupagus for PHP hardening
The virus scanners search your apps, operating system (OS), and even the kernel for suspicious files and changes. The firewalls close unneeded network ports and mitigate denial of service (DoS) attacks that can lead to extended downtime. Learn more about CWP security scanners.
Some plugins mentioned above are only available with CWPpro. Free CWP users can install and manage the base software from the terminal.
Miscellaneous Security Tips
Since there’s no TFA in CWP, it’s important to implement other brute-force countermeasures from within the OS.
In “/etc/security/limits.conf” you can further restrict user capabilities including how large a file one can create.
The “/etc/login.defs” file is where you can develop strict password policies like forcing users to reset their password after “X” amount of days.
Configure “/etc/ssh/sshd_config” to change your SSH port number and disable password authentication for greater defense against SSH-based attacks.
You might want to consider installing pam_cracklib or libpwquality Pluggable Authentication Modules (PAM) from your OS repository to prevent users from using insecure passwords while you’re at it.
So, How Secure is Control Web Panel?
Fairly secure, if you put in the work to learn how to use the security functions at your disposal. Even without knowing how to harden a Linux system, the base installation will still provide some protection for your cloud server setup while exposing you to many security features. If you ever have questions about hardening your CWP server, contact our Live Support at any time.
Upgrade to VPS Hosting for Peak Performance
Upgrade to InMotion VPS Hosting today for top-notch performance, security, and flexibility, and save up to $2,412 – a faster, stronger hosting solution is just a click away!
SSD Storage
High-Availability
Ironclad Security
Premium Support

