Table of Contents
In this article:
Checksums
Defense in depth involves layers of security, and file management is a core part of it. If you offer or recommend downloadable content, it’s important to understand the importance of verifying checksums on your Linux server, PC, or Mac. Whether you use a content managment system (CMS), framework, or static HTML, you must be proactive to mitigate the possibility of any malicious activity affecting end users’ workstations. Providing checksums for end users to ensure their downloads are legitimate is one way to do this.
Below we’ll cover some best practices for implementing checksums.
Want better server security? Our VPS Hosting has over a dozen security features between cPanel and WebHost Manager (WHM). Our Dedicated Hosting plans offer a hardware firewall.
Checksum Practices
Store Checksums on an External Site
We often recommend storing verified backups on at least two other devices. Download your cPanel backup to a computer that’s backed up regularly. Now, you have 3-4 backups including the server (and WHM backup for VPS / Dedicated servers). This disaster recovery practice provides redundancy that protects you from most data corruption and intrusion issues.
Similarly, its best to list checksums in an external location to protect users against malicious files. Otherwise, if your website is hacked, someone can change the file (and/or destination to it) and the checksum with the same credentials to appear valid. Something similar happened to Linux Mint a few years ago. Their long list of download mirrors (externally hosted web servers) reduced the impact as users had multiple download options. A hacker isn’t likely to be able to hack all available download mirrors.
Recommended: Host a checksum list on your website and another reputable platform such as Gitlab and Github
Multiple Checksums
After you identify multiple locations to show your checksums, make sure you include the strongest hash algorithms. SHA512 is the strongest commonly supported SHA function as of 2019. It’s preinstalled in many popular Linux installations. The lesser SHA384 is popular with subresource integrity (SRI).
MD5 and SHA1 algorithms are fast but not recommended because they’re weak and prone to hash collision. Users without command line access can be directed to websites suh as VirusTotal.com and SRIhash.org.
Recommended: Provide checksums starting with the strongest hash – e.g. SHA512, SHA384, SHA256, MD5
Instructions
Concise instructions can ease less technical users intimidated by the command line interface (CLI). Whether you instruct users to use a website or CLI, multiple checksums may discourage users from verifying their download.
To mitigate this, provide clear steps with CLI commands a user can copy and paste with screenshots, how to compare their checksum to the original, and troubleshooting tips. If you recommend Virus Total or a similar tool, provide a quick GIF or video explaining how to navigate the website.
Recommended: Clear copy-and-paste steps, screenshots, troubleshooting tips if it does not match the expected checksum
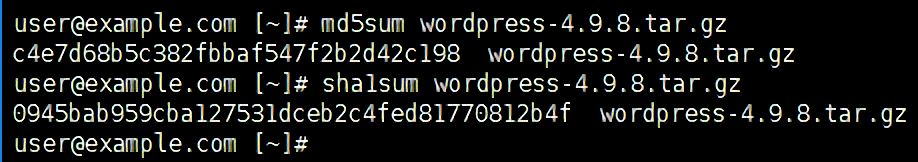
Here’s an example from our Linux checksum guide:
Overall Hardening
As a general tip, research ways to improve security within your website, .htaccess file, server, and DNS records. Many CMSs have security plugins. There’s also online tools such as Mozilla Observatory for .htaccess hardening.
Recommended: Follow best security practices for your CMS and server.
Privacy Policy
Your site may be the first to teach a new user about hashing for file verification. It could create a positive impression on technical visitors. There’s one major thing that can cement that impression and cover legal matters: a human-readable privacy policy that’s easily accessible on every page.
Also, all websites – not just e-commerce sites – can benefit from working towards General Data Protection Regulation (GDPR) compliance. It shows you care about user privacy and personally indentifiable information (PII) in case of an intrusion. Many popular CMSs added privacy features for easier compliance following its implementation in 2018 – WordPress, PrestaShop 1.7, MatomoAnalytics, etc.
Recommended: Work towards GDPR compliance to support user privacy
Realize That Some Won’t Use it
Security and convenience many times clash, as if on a balancing scale, with convenience winning in the end. However, you should facilitate better security practices to the best of your ability. One’s privacy and peace of mind are valuable with the current cyber threats. Do your part to help provide that.
Recommended: Remember, user error is the most vulnerable attack vector
Security [is] everyone’s job. Technology cannot negate user error.
6 Ways to Secure Your Web Activity from Your Computer
Learn more about improving security from our partners at Sucuri.
