Table of Contents

Monarx Security is a top-notch anti-malware solution that safeguards websites and applications developed using PHP and other programming languages. With its comprehensive threat detection and prevention system, Monarx Security protects against a wide range of threats, including web shells, adware, phishing, mailers, and more.
If you’re an InMotion Hosting customer, you can watch Monarx Security activity for free through the cPanel, WHM, or Control Web Panel interface. However, it’s worth noting that Monarx Security is currently available for Shared Hosting and Managed VPS Hosting plans.
Wondering what exactly Monarx Security does? Keep reading to find out!
- What is Monarx Security?
- How to Access Monarx
- Monarx Dashboard
- Submit File for Review
- Additional Security
What is Monarx Security?
Monarx is a unique type of next-generation web firewall (NGFW). It is focused more on the behavior of PHP code, not just how it looks or its signature, both of which can be obfuscated (e.g. polymorphic viruses). This mitigates the possibility of files being falsely marked as malicious, which can lead to issues in clean websites, and decreases the time required to detect zero-day vulnerabilities.
Monarx consists of four main components:
- Protect – tracks web shell payload deposits and blocks execution
- Hunter – scanning module that finds existing issues
- Dashboard – web-based console for viewing detection
- Agent – a server-side agent that runs Monarx modules and manages detection information configured and sent to the Monarx Cloud.
Here’s how the actual process works.
- Monarx Security is installed on the hosting server. The agent consists of two modules. Protect tracks and blocks execution of web shell payloads. Hunter runs full, real-time scans for compromised source binaries and web shells weekly.
- The Monarx agent downloads security rules related to web apps and content management systems (CMS).
- Files flagged as malicious by the Monarx agent are automatically processed per security rules and sent to the Monarx Cloud for further analysis. This helps to preserve server resource demands.
- PHP-based web shells/backdoors are blocked from executing, a technique they dubbed “post-exploit payload prevention.”
- Our system administrators can use the Monarx API for greater Security Information and Event Management (SIEM) across all shared hosting accounts to detect code injection and similar attacks more effectively.
As you can see, this software-as-a-service (SaaS) does a lot in the background that isn’t common with other web application firewalls (WAF). The best part about it: you can check Monarx activity in cPanel but don’t have to configure anything. Just know that it’s there.
What is a Web Shell?
A web shell is malicious software used to access a system remotely without authorization. Web shells constitute a significant threat because they’re hard to detect while allowing hackers administrative access to do whatever they please, such as:
- Website defacement attacks
- Distributed denial of service (DDoS) attacks
- Privilege escalation to access restricted services
- Anything else an authorized root user can do
There are three types of web shells:
- Bind shell: the victim’s system is infected to listen on a specific port (a standard backdoor).
- Reverse shell (connect-back shell): the system is infected to actively seek a connection to the cyber attacker’s local machine or command and control (C2) system.
- Double reverse shell: a reserve shell where the target machine uses separate ports for input and output.
The typical steps an attacker takes to accomplish this are as follows:
- Exploit a vulnerability to upload a web shell (payload) to a target machine
- Move the web shell to a more accessible public directory
- Access the web shell to upload or modify files
In summary, preventing web shell execution reduces the possibility of manipulating your website for crypto mining, spamming, and other malicious purposes.
How to Access Monarx
Monarx has no control interface in either the WHM or cPanel. You can access a dashboard when it is present and running on the server. You can see the verification that Monarx is running and a report if malware is detected.
See our article on How to Use Monarx Security’s “Detect” Mode.
cPanel Access
Here are the steps you must follow to access Monarx through cPanel:
- Log into cPanel.
- Select Monarx Security under Security.
- Refresh the page if you see the following message: “Monarx is still attempting to provision your account. Please refresh the page. If the problem persists, check back later.”
WHM Access
For WHM, you can access Monarx by searching for it through the web interface:
- Log into WHM.
- Use the Search field and type in “Monarx.”
- Monarx Security will appear in the left-hand column. Click on it to open the dashboard.
CWP Admin Panel
Here are the steps to access Monarx through the Control Web Panel Admin Panel:
Note: The Monarx dashboard is only accessible via the Admin Panel on CWP servers.
- Log into the CWP Admin Panel.
- Select Monarx Security under Security.
- Refresh the page if you see the following message: “Monarx is still attempting to provision your account. Please refresh the page. If the problem persists, check back later.”
Monarx Dashboard
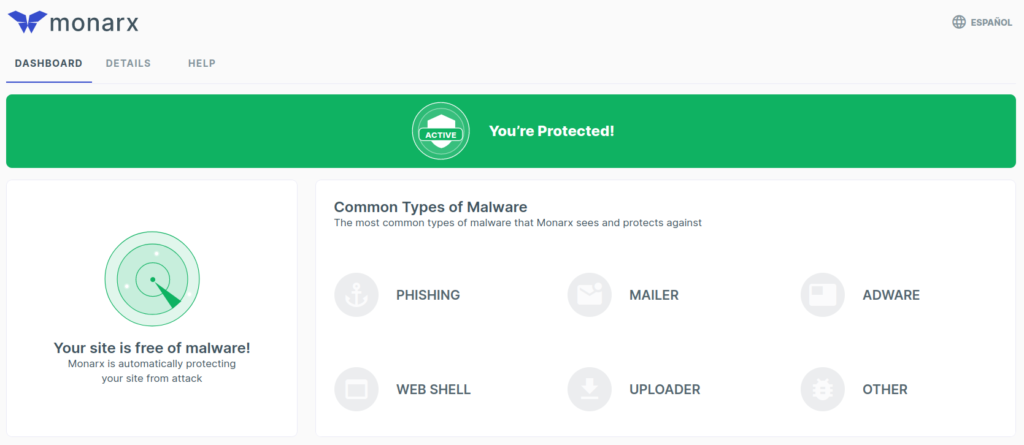
Typically, the Monarx dashboard will state that “you’re protected” and “your site is free of malware!” If not, contact Technical Support to upgrade Monarx from “Detect Only” mode to “Protect” mode. On the right side is a list of what types of malware Monarx fights automatically:
- Uploader access to your server
- Web shells that enable advanced persistent threat (APT)
- Phishing and cybersquatting sites injected into your server
- Mailer applications for spoofing your email accounts
- Adware scripts embedded into your site
- Other malware that can infect users that visit your site
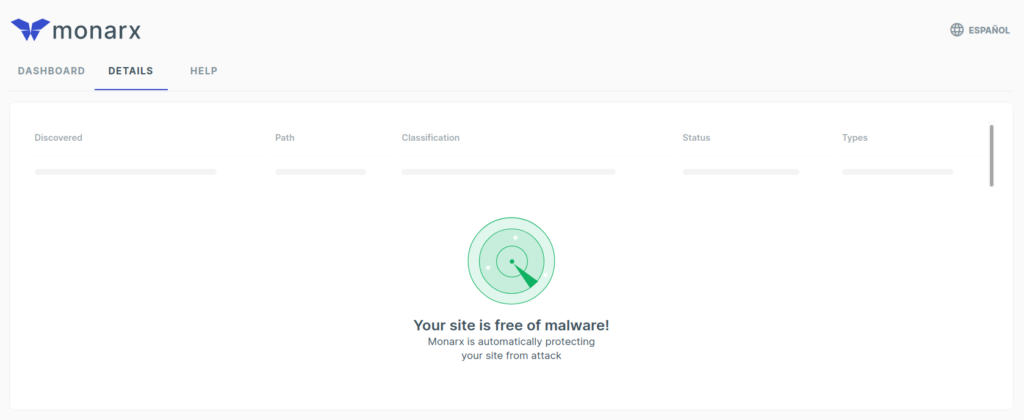
Select the “Details” tab to view files on your cPanel server that are marked as suspicious.
- Date and time discovered
- Absolute file path
- Classification (malicious or compromised/infected)
- Status of the file (quarantined, blocked from executing, cleaned of malware, or logging for further action)
- Type
Submit File for Review
There is one interactive feature for end users at this time. If at any point you find that a compromised file was incorrectly marked as clean by Monarx, you can submit the file for further review. Follow these steps:
- Log into cPanel Terminal, terminal in the CWP Admin Panel or SSH using a terminal client of your choice.
- Use the following command (replace “filename” with the actual file name):
Monarx software captures further information related to malware detected, including:
- File SHA-256 checksum or stronger
- IP address and country of origin
- Affected web applications (e.g. CMS plugins and themes)
The “Help” section includes additional information on the Monarx cPanel interface and malware in general. If you need further assistance, contact Technical Support.
Additional Security
Monarx isn’t a defense-in-depth security suite. You still should have a traditional firewall, a Web Application Firewall for your web applications, and antivirus software.
If you upgrade to a VPS or dedicated server, you’ll need to manage your security posture more effectively.
- Ensure an AV scanner (ClamAV or ImunifyAV) is installed and set to scan weekly.
- Harden your traditional firewall. We recommend ConfigServer Security & Firewall (CSF) or Firewalld.
- Protect your server with a signature-based firewall such as ModSecurity or Fail2ban.
Monarx provides advanced malware detection (“Insight Only” mode) and protection (“Protect” mode) for your web server. It works without any interface with the website administrator and allows the reviewing of a suspected file. Its lightweight footprint and operation without user input make it a valued solution for protecting your server.
