In this article we’ll discuss how to clean up a code or script injection that might have occurred on your website that is causing it to try to load malicious content to your visitors, or preventing your site from displaying properly.
Typically code injections are carried out by an attacker uploading a PHP shell script to your account, either by compromising your FTP credentials, or by exploiting usually outdated software that you might have running on your website.
Below are steps for cleaning up a wide spread script injection that occurred on a WordPress site. We could tell that something went wrong because when we tried to view the site today it was simply showing a blank page, and when we went in to investigate it was obvious that a code injection had taken place.
It’s important to note that this would be considered an advanced task and you can only do this with a VPS or dedicated server plan. Additionally we can’t take any responsibility for further damage you do to your website using this clean up method, so if you don’t feel comfortable doing this be sure you make a full backup of your account prior to following these steps or contact our support team for help.
Cleaning a Code Injection Attack
- Login to your server via SSH.
- Navigate to the user’s /public_html directory with the hacked website with the following command:
cd ~userna5/public_html/ - Now open up that sites index page, in this case index.php using the vim text editor with the following command:
vim index.php -
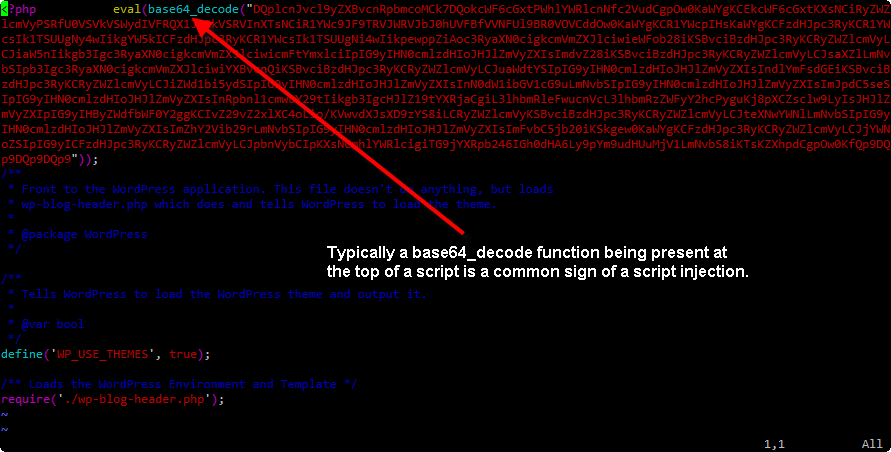
It should be very obvious at the top of this file that there has been a script injection, usually one of the tell tale signs of a script injection is having a base64_decode function mentioned, especially if it’s at the top of a bunch of scripts.
You’ll want to copy the text starting at eval(base64_decode and grabbing about the first 10 or so characters, in most SSH clients simply highlighting text will copy it to the clipboard.

- Now you’ll want to type in the following command using the text that you copied from the /public_html directory:
grep 'eval(base64_decode("DQplcnJvcl' ./ -Rl > HACKSThis will take some time to complete as it’s going to look through all of your files for that string, it will be placing them in a file called HACKS.
- Now using that HACKS file in a loop, we want to create a backup copy of each injected script with the suffix -HACKED using the following command in case when we are stripping out the injection it happens to grab any good code accidentally:
for hackFile in `cat HACKS`; do cp -frp $hackFile $hackFile"-HACKED"; done - Now we can use the same loop, but this time using the sed command to replace the code injection of each original file:
for hackFile in `cat HACKS`; do sed -i 's#<?php.*eval(base64_decode("DQplcnJvcl.*));#<?php#' $hackFile; doneWhat this sed command is doing is using the -i flag for an in place replacement, the ‘s# part is telling it we’re doing a string replace, with the # symbol being the delimiter of our strings.
The next part is the sting we want to replace, it begins with <?php then we are using .* to state any character at all, followed by eval(base64_decode(“DQplcnJvcl which is the part of the injection we had copied earlier, then finally it ends with another .* to grab all of the rest of the text till finally the last part of the string )); is encountered.
After the second # we put the string we want the first string to be replaced with, in this case just <?php, then we finish up the sed command with another #’ then we put $hackFile after the
full sed command since that will be the file name of the current file in our loop.
Now try to load your site again and hopefully it is back to normal. Depending on the severity of the code injections sometimes this won’t be enough to clean it up, but in most cases this should do the trick.

I have tried your steps mentioned above but couldnot got result as expected . I see the HACKS file but its empty. can you please help to get rid of this please
This depends on the attack itself. This is a public forum, so we can’t exchange any acount-related information. I advise contacting our Live Support team.
Thanks a lot for the article. Saved me a lot of searching and tryings. Very thoughtfull.
hand how to find the Entry-gate of the injection??
At 3:00 the injection comes, at 4 I clean the pages. daily
Kind of agreement….
You will need to contact our live technical support team for more information on the issue. I would recommend sending a ticket. You need to provide the information about your account and what you are looking for. You can see the contact information at the bottom of the screen.
This is awesome. I had a sister wordpress site on a subdomain that leeched to other static info pages. Just awesome, thank you!
“my index.php file is getting deleted every night, could you please suggest, how to identify the root cause.”
As a previous poster, I have the same problem and have performed all tasks advised in your “Recovering from a Hack”. Do you have any advice to resolve?
I don’t think that I can do either of the recommendations as I am on shared server:
“I recommend reviewing the FTP, and Access logs for record of the file, or access to your cPanel.
You can also perform a shell scan for malware with the following steps:
Run the command:
shellscan
Hello JLK,
If your files are getting altered every night, then you need to review your system for possible security issues. You should also speak with our live technical support team in order to make sure your site is scanned. In regards to your system, if you are not familiar with system security and making sure that it’s virus-free, then you should speak with a local IT expert who can help you evaluate your computer to make sure that your system and login information is not compromised.
If you have any further questions or comments, please let us know.
Regards,
Arnel C.
Note to others… you can make this into a shell script .. but! remember to exclude your .sh file or you’ll overwrite you own shell script …. guess how I figured this out!
Hello john paul,
Can you please send the script to find the malware/php code injection?
It would be appreciated.
Vincent, as this code was written as an internal tool only, we are unable to provide the source code for it.
This solved my problem, i was looking for a solution for 2 days. Thanks!
That’s it … thanks dude.
Super helpful at identifying backdoor insertion after Drupal was compromised about 6 months ago. Created some scripts based on this that I have running periodically ona cron job. Have caught problems that way since. Thanks!
Hello Crashby,
Thank you for contacting us. We reviewed the command, and it should not have a problem with spaces.
Can you provide the specific code you are running?
Thank you,
John-Paul