Table of Contents
If you are a website administrator, security should be at the top of your list. That’s why your first step should be to work with InMotion’s WordPress Hosting team to get your website up and running. After that, you can lock down the WordPress admin login with some .htaccess rules to prevent unauthorized login attempts.
How to Locate Your .htaccess File in cPanel’s File Manager
This guide will show how you to limit WordPress admin login attempts by IP address, or referrer. Below we’ll show you, how to get to your .htaccess file, and what edits to make, to limit WordPress admin logins. But first, we’ll show you how to find your .htaccess file in the cPanel File Manager.
- Log into your cPanel.
- Find the Files category and click on the File Manager icon.
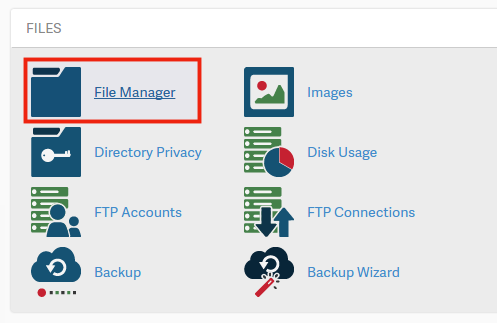
- Click Settings at the top right corner.

- Select the Document Root for your domain and check the box next to Show Hidden Files. Click Save.

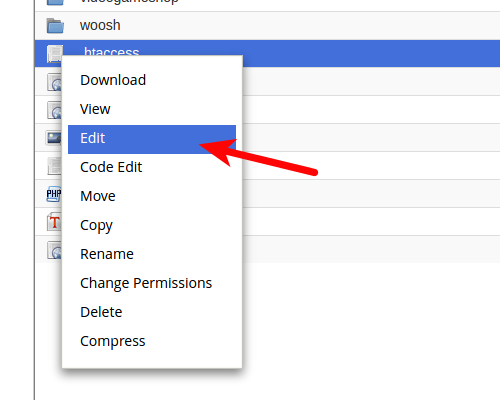
- Right-click the .htaccess file and select the Edit option.

- If you have a text editor encoding dialog box pop up, simply click Edit.
How to Restrict WordPress Admin Access
The following rules should be placed at the very top of your .htaccess file.
- Secondary WordPress admin .htaccess password (Recommended if your IP changes)
- A Single IP Address
- Multiple IP Addresses
- Dynamic IP Address Access
Single IP Address Access
You can check your IP to get your computer’s IP address.
If you are using CloudFlare or a DNS level filtering service, this method won’t work, you’ll want to setup a secondary WordPress .htaccess password for protection instead.
To allow access from a single IP address, replace 123.123.123.123 with your own IP address:
Multiple IP Address Access
You can check your IP to get your computer’s IP address.
If you are using CloudFlare or a DNS level filtering service, this method won’t work, you’ll want to setup a secondary WordPress .htaccess password for protection instead.
To allow access from multiple IP addresses, replace 123.123.123.xxx with your own IP addresses:
Dynamic IP Address Access, Limit by Referrer
If your IP address changes, you can protect your WordPress site by only allowing login requests that come directly from your domain name. Simply replace example.com with your own domain name Most brute force attacks rely on sending direct POST requests right to your wp-login.php script. So requiring a POST request to have your domain as the referrer can help weed out bots.
Wait at least 15-20 minutes, and try to log into your WordPress site again. If you try to access the WordPress dashboard within the 15 minute window of a block, this could extend the block longer.
It’s important to wait for the previous block to expire and be patient before attempting to access your WordPress site again. You should now be blocking unauthorized WordPress admin login attempts utilizing .htaccess rules.


I’m sorry to see that you are experiencing issues with this and that the Support agent was unable to assist you properly. Unfortunately, the public forum is not the most secure place to reach out for Support. This guide outlines a few methods, however, you do not need to implement them all. I recommend testing each process and following the links in this guide if you continue to experience issues. You may also contact our Live Technical Support to assist you with this as well.
Please also note: You may always submit your feedback for specific interactions with Support Agents through your Account Management Panel, which will be delivered to their managers/supervisors to ensure a consistent and exceptional Technical Support experience.
Hello,
If you want your web server to be the referrer, then you should use the Dynamic IP address access, limit by referrer option above. It will limit it based on your domain name though the IP address may have changed.
If you have any further questions or comments, please let us know.
Regards,
Arnel C.
Hello Tabitha,
Actually, those screenshots are of the newest version of cPanel theme Paper Lantern. If you’re seeing something different, can you please tell us (or show us) what you’re seeing? If you have any further questions or comments, please let us know.
Regards,
Arnel C.
I already have some code from wordpress itself in my public_html/.htaccess file.
Hackers can still getting to wp-login.php once, after which they are blocked by the htaccess rule. Could it be due to having two instances of <IfModule mod_rewrite.c> and RewriteEngine On . Should they be merged?
I removed the wp-admin rule becuase it conflicted with the wp-statistics plugin.
At the moment I have:
# BEGIN LIMIT WP-LOGIN.PHP BY REFERRER
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{HTTP_REFERER} !^https://(.*)?my-domain\.com/(.*) [NC]
RewriteCond %{REQUEST_URI} ^/wp-login\.php(.*)$
RewriteRule ^(.*)$ – [F]
</IfModule>
# END LIMIT WP-LOGIN.PHP BY REFERRER
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ – [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
I like this solution and it has helped my issues but the people I ask to provide their IP addresses so I can grant them access keep getting the IPV6 version…this only works with IPV4 addresses. I’ve noted the trend is hard towards the IPV6 and it’s getting hard to find your IPV4 address sometimes. Is there anyway to make it work with both…or even switch this solution to all IPV6?
Hello David,
Thanks for the question about using IPV6. Currently, most networks are still using IPV4, so you may want to stick with using the solution using that version. The use of IPV6 would require a code to change to the IP address format as well as the command. Please see this forum post. It discuss the command to use IPV6. Remember that anytime you create rule/condition that it operates from top to bottom.
If you have any further questions or comments, please let us know.
Regards,
Arnel C.
Hi,
I am impressed how helpful you are. I also run a blog, so I also try to be helpful for my readers . 😉
I changed the URL of my login page. Now I want to ban immediately for 2 hours every user who enters the URL “…/wp-login.php” or “/wp-admin”. It would save a ton of CPU of my server! How to do this on the server side (I don’t want bots to hit my WordPress)?
Simon, that’s a great idea! This would basically turn the default login page into a ‘honeypot‘ for malicious visitors or scripts. For a server-side option, if you have root level access to your server, and you have CSF installed you could write a simple script to trigger a CSF command like
csf -td $IP 7200. If you’d like a plugin to do so, I recommend reviewing the options in the Wordfence security plugin for WordPress. However, the CSF option would have the advantage of being CMS agnostic, but the disadvantage of requiring root level access on the server, which isn’t always an option.Hi, i want to change https://mysite.com/wp-admin and https://mysite.com/wp-login.php to https://mysite.com/customname
please help
Plugins are not working for me.
Regards
If the conventional plugins are not working, you can add a custom WordPress function to your theme.
Hello,
I must have a bot trying to access my site today, but I also tend to get sporadic login attempts that might be real people using the login page. Can I combine the “limit by referrer” and “single IP address access” methods so that bots AND people other than myself are blocked? I’ve tried the methods listed here and every time I hit “save” I get another lockout notification. The only thing I’ve found that stops them is this script I found on another site:
# Block access to wp-admin.
order deny,allow
allow from 69.145.177.48
deny from all
Unfortunately, it completely disables my website – not just the login page. I’ve left that in the .htaccess file for now until I can find a solution. Please help! The website is chandlercommunications.com. Thanks!
Hello,
Can I re-write the below code that if users dont have access swould be sent to particular page and not to 403 page?
[code]
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteCond %{REMOTE_ADDR} !^123\.123\.123\.121$
RewriteCond %{REMOTE_ADDR} !^123\.123\.123\.122$
RewriteCond %{REMOTE_ADDR} !^123\.123\.123\.123$
RewriteRule ^(.*)$ - [R=403,L]
</IfModule>
[code]
Hello,
For the last line of the rewrite you should be able to use something like this.
RewriteRule ^(.*)$ https://www.example.com/$1 [L,R=301,NC]
Best Regards,
TJ Edens
I’ve used this code which i have found on other posts but it doesn’t work, when i add with my ip it appears to work, what i mean by this is if i don’t include my ip range it blocks access, Great however i am still getting hacking attempts which indicates it doesn’t work.
Hello Alan,
Thank you for contacting us. I recommend reviewing any other rules in your .htaccess file, to ensure they are not interfering with these ones.
Also, keep in mind this rule will block access, but the hack attempts may still continue. It really depends on the nature of the attack. How are you viewing the hack attempts?
Thank you,
John-Paul
hi
my isp regularly change my ip address, can i define ip range?
Hello Alireza,
In the case of needing a range or a large number of specific IPs, you would want to go with the ‘limit by referer’ option.
Kindest Regards,
Scott M
This is not working. Well, let me rephrase that… it works, but the hackers are getting around it.
I added this code to my .htaccess file:
RewriteEngine on
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteCond %{REMOTE_ADDR} !^123\.123\.123\.123$
RewriteRule ^(.*)$ – [R=403,L]
Obviously, replacing the 123.123.123.123 with my IP address. IT WORKS!
I tested to make sure it was block other IP address by changing it to an IP that is not mine. IT WORKS!
I block me from admin login.
Why are the hackers still getting through????
I keep getting these emails from WP Limit Login
4 failed login attempts (1 lockout(s)) from IP: 91.146.107.31
Last user attempted: admin
IP was blocked for 15 minutes
Ok, I looked up the files these IP’s are accessing…. how they are getting to wp-login from this file I have no clue. The file is:
xmlrpc.php
I put the follow at the top of my .htaccess file:
Order allow,deny
Deny from all
lets see if this stops it.
Thank you so much. That worked.
It’s official, you are definitely smarter than my current host. Maybe I should start to consider my options…
Yes, I could, however I have a dynamic IP, so I do not want to take that route.
Hello Ted,
You are correct, technically they can hit that file and get a 200 response code. The first example below will block any request with a url that ends with wp-admin (in regex $ means ends with).
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
However if you changed it to what is below it will block any request that has wp-admin in the url:
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin*
Best Regards,
TJ Edens
Hi,
I have used your example code:
<IfModule mod_rewrite.c>RewriteEngine onRewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$RewriteCond %{REMOTE_ADDR} !^123\.123\.123\.123$RewriteRule ^(.*)$ - [R=403,L]</IfModule>and it seems to almost work on my enviroment.
It blocks access to wp-login okay, but why am I seeing ‘success 200’ notifications on my logs, when someone tries to access admin-ajax.php? Shouldn’t that be blocked too?
Here’s a sample of my log.
109.201.135.7 - - [03/Aug/2015:01:31:17 +0300] "POST //wp-admin/admin-ajax.php HTTP/1.1" 200 1 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.31 (KHTML, like Gecko)"Am I missing/misunderstanding something?
Hi. I tried what the code said and it did not work it just blocked me out saying 505 error. Me and a friend keep getting locked out all the time and we cant make this site. Can you please help? This is getting beyond a joke and we would like to make our site
Hello Patric,
This works for most people. If you are still having issues, you may want to contact Live Support so that they can help you with anything else that may be specific to your account.
Kindest Regards,
Scott M
First let me start by thanking you for your great post. Now, my to my situation.
I have a bit of a complex environment. In its simplest form, I have two file servers connected to the same DB server. Lets call them FS1 and FS2. Both FS1 and FS2 are mirrors to each other except their .htaccess files. Both file servers have their own unique URL, something that looks like this: fs1.somesomedomain.somedomain.com and fs2.somesubdomain.somedomain.com
When you go to my domain, for example, to www.mydomain.com, it will redirect to FS1. Which will take you to the fron end to my WordPress site. If you want to go to the backend, then I will go to the FS2 domain directly. I am the only one accessing the backend.
Now, I would like to completely restrict access to the backend in FS1. How do I do that? Do I restrict access to wp-login and wp-admin? What about the .htaccess file, what rwx restrictions does it have?
Hello Bob,
Are you able to set an htaccess file on the back end server and limit it to your specific IP?
Kindest Regards,
Scott M
I have my .htaccess file and would lik for someone to look at it and see how I can go about locking it down. I currently have installed Bulletproof Security which I thought already covered this but maybe not. Please advise on how to attach it here if possible.
Hello Jeremy,
Thank you for contacting us here in the public forums. The above guide explains how to successfully lock down your .htaccess file, and provides specific examples. But this is not necessary if you are using a Bulletproof security.
The BulletProof Security plugin secures your .htaccess and other files in your WordPress site. Here is a link to our walk-through guide on the WordPress BulletProof Security plugin configuration.
Thank you,
John-Paul
I live chatted with your support today and could not get the answer to this….
I have a 2nd domain under my hosting accnt with WPress installed in that subdomain. I have a htaccess file with just MY ip and IMH ip in there which is located on my ROOT dir, which SHOULD protect my whole site and sub domain… right ? I created a new user with user/pass for another person who is helping with the subdomain design. THEIR ip is NOT in the htaccess file but they are still able to log into the subdomain’s WPress admin, when I thought the htaccess would prevent them from doing that UNTIL I added their ip to my htaccess. They can log in fine with being in the ip list so I am losing all confidence in this htaccess ip restriction thing since its not working !!
What is going on to let someone inside that is NOT on the ip htaccess file ? Even if they have a good user/pass they still should NOT be able to log in.
Thanks
Paul
Hello Paul,
Thank you for contacting us. We are happy to help, but we will have to see your .htaccess code to help troubleshoot further.
Please provide the content of your .htaccess code, so we can help narrow down the cause.
Thank you,
John-Paul
Hi Arn.
I tested the two lines of your code which test the URI, separately (I commented one line while testing the other), and I realized that one of them is ineffective: the line which tests the presence of wp-admin folder on the URI.
If I type https://localhost/wp-admin in my browser, I will receive an “access denied” message. But, if I type https://localhost/wp-admin/ (note the slash at the end), I will gain access to the wordpress login page.
This problem can be corrected if you change this line of code as follows:
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin(.*)$
Note: as an URI with wp-admin is automatically redirected to an URI with wp-login.php, the ineffectiveness of this line of code does not imply in any security flaw in your code: it is just a question of performance (the user will not need to be redirected to an URI with wp-login.php to be blocked).
Regards,
Aldemar
Hi there. I’m going to attempt the single IP access. However, I have a question regarding stats. Using these blocking methods, when my site gets hammered by attempts, will these show in awstats or other stats? As in, will I start seeing massive amounts of 404 page errors, etc? I am hoping to have a clean solution, but it’s not clear to me what happens to the www.mysite.com/wp-login.php requests after I prevent all IP addresses other than my own. I would great appreciate insight into what happens with stats, after this solution is implemented. Thank you.
Hello Douglas,
Thanks for the question. This security option will not affect your stats as the stats are generally for successful connections to your website – not for attempts.
I hope this helps to answer your question, please let us know if you require any further assistance.
Regards,
Arnel C.
I have inserted the “Single IP” code in htaccess on multiple occasions. The login works during this first session. Then when I go out to the worpress site, any pages except the home page are returned with 404 error codes and cannot be accessed. If I go to the “Permalinks” and resave the settings using %postname%, these pages come back active and accessible. But, then I go back and check the code in my htaccess file and it has automatically returned to the standard WP settings. My limiting code to only allow my IP Address is gone.
Is there some special place in the coding, this needs to be installed? I read in a forum that anything between the #Begin WordPress and #End WordPress will be automatically changed by WordPress, which is reflected with my problem.
I also see a future problem in that we are going to have a newsletter and vendors pages which will require selected visitors to be able to have a username that allows them to visit protected pages. I keep reading this cannot be done if I protect the login and admin using the process you have listed above.
This is becoming a real pain in the butt with all of the attempted attacks every friggin day on WordPress sites. Insanity. I am hoping there is some simple solution to these issues? My goal is to stop the hackers from gaining access to any of the files on the server in a WordPress site, especially the login and admin files. But also allow real visitors, customers and clients to be able to access protected pages.
Thanks,
DG
Hello DG,
When you insert the single IP code, it should NOT be in the WordPress. As you have noted, it will automatically be removed. Add the code before the #Begin portion of the WordPress.
I also see a future problem in that we are going to have a newsletter and vendors pages which will require selected visitors to be able to have a username that allows them to visit protected pages. I keep reading this cannot be done if I protect the login and admin using the process you have listed above.
The login protection is FOR the Administrator login. If you have a newsletter and vendors pages, they shouldn’t require an Admin login. If so, then you can use a different method for limiting who can have access if necessary. There are several other methods provided above.
I hope this helps to answer your question, please let us know if you require any further assistance.
Regards,
Arnel C.
Hi,
Im facing lots os spammy referal traffic on my wordpress website detected by Analytic Tools. Spammy websites are as:
bestwebsitesawards
darodar
ilovevitaly
hulfingtonpost
buttons-for-website
semalt
priceg
Now wanted to prevent these type of spammy referal traffic but don’t know how to do. Read some where that can be prevented through htaccess but the structure of wordpress htaccess is different and when trying, it cause problem on website sometimes 500 internal services error sometime some other.
Please help me if any one have solution.
Herein the Website – https://www.*******.com/
Hello Spar,
Thank you for your question. Please see our guide on how to Block unwanted users from your site using .htaccess.
You will have to review the existing rules in your .htaccess file to ensure they are not interfering with the codes you are adding. A good developer should be able to assist you with this.
If the traffic is originating from spammy backlinks, you can use Google’s Disavow tool to have them ignore certain links.
If you have any further questions, feel free to post them below.
Thank you,
John-Paul
Actually, you need to be a little precise when defining WordPress being in a folder.
There’s xyz.com/some-folder-name where WordPress completely resides in that folder and is independent of whatever is going on in the root of the site. i.e. The path to WordPress would be xyz.com/some-folder-name/index.php. For that, what Scott mentions is correct.
Then there is what’s commonly called “WordPress in a folder”. In this instance, like the previous example, all of the WordPress files are installed in the folder e.g. xyz.com/some-folder-name. However, in this case WordPress is configured so that the index.php and the .htaccess files for the site have been copied from the folder and reside in the root of the site. In this case the path to WordPress would be xyz.com/index.php.
In this case, the place to tweak the .htaccess file would be xyz.com/.htaccess, rather than xyz.com/some-folder-name/.htaccess.
More about this can be found at https://codex.wordpress.org/Giving_WordPress_Its_Own_Directory
How would I use the first choice “Single IP address access ” to allow a range of IP addresses? I’ve tried the CIDR xxx\.xxx\.xxx\.xxx\/xx and that doesn’t work. Nor does xxx\.xxx\.
How can I allow a range?
Hello Ken,
In the case of needing a range or a large number of specific IPs, you would want to go with the ‘limit by referer‘ option.
Kindest Regards,
Scott M
I am not sure if I need to alter the .htaccess file which is inside the ‘wordpress’ folder for my site, or if I need to create one at the top level of the domain?
Can you advise please?
Hello Robcnz,
If the WordPress is installed at the domain level then you would alter that one. If you have it installed in a subfolder, such as example.com/wordpress, then you would create/alter the .htaccess file in the wordpress folder.
Kindest Regards,
Scott M
Hi, Ive been using your referrer code method to prevent remote attampts to login successfully for some time now – with a focus on one of my accounts add on domains. In the past month however it doesnt seem to be working. Today I’ve tried the limit IP address login as a test and it too doesnt seem to be working – loaded the IP address of my office computer and then was able to log in from my cell on diff IP address…. Any thoughts on why neither of these would be function as I would expect or as the prevsious referrer block method did? thank you.
If you are limiting your login using .htaccess exactly as in this article, only the IP addresses defined should be able to get in. Be sure that your phone is not connected via wifi when testing as it would caused you to have the same public IP as your computer.
thank you very much – resolved on the other thread – caching issue and tested on the wp-admin versus the .com/login page
Why not try a plugin https://www.sourcexpress.com/wp-double-protection/ which can be installed on a wordpress site and instead of taking the risk of changing .htaccess file, we can have an extra layer of protection with these plugins.
Hello Kumar,
Thank you for your suggestion. Feel free to submit a post in our User Submitted section, then I can link to your article.
Thank you,
John-Paul
Swap the order of the deny and allow:
Order Deny,Allow
Deny from All
Allow from <ip address>
Hello Shannon,
Thank you for contacting us. When you hit Edit you will then be able to edit/add text to your .htaccess file.
Then, add the rule you want to use (they are in the black boxes above), and update them as needed. For example you may want to add your IP to the rule, instead of the existing one.
I hope this helps,
John-Paul
I was having problems with membership levels and thought that it was restrict access pro that was causing the problem so I deleted both plugins and now I cannot access the dashboard nor login in to my website.
Can you help me?
Thanks.
Hello,
Unfortunately, your issue is nothing we can identify with the information given. I am unable to see your site or locate an account. Did you remove the plugins via the dashboard or did you delete them in the file structure? What type of errors are you getting when trying to log into the wp-admin?
Kindest Regards,
Scott M
After clicking “edit,” I have no idea what this article is talking about. I don’t see something similar on the screen it’s referring to, and I’m so unfamiliar with this type of thing that I’m just totally over my head.
This is the most useful article I have been able to find on securing a WordPress site.
Hi Staff,
I am attempting to use the trusted referrer option and I am still not able to login. The site is www.readysetloan.com. I cannot figure out what I am doing wrong and have been locked out since Thursday.
Thank you – Eric
The referrer option disallows bots from sending POST requests directly, however, if the brute force attacks are fully hitting your wp-login.php page, this will not work. I recommend allowing by IP if you continue to experience issues. Keep in mind that it can also take about 15 minutes for the block to be lifted after putting the protection in place.
Just a bit more specificity for those unfamiliar with code. I was attempting to block false login attempts on my site from a brute force attack and the file stated to use the IP address at the top of the document — I didn’t know if that meant at the very top of the document or under the comments of the document.
Very frustrated. I’ve done: secondary password protection of the wp-admin directory and referral restrict in htaccess. I don’t have admin as a username, yet still I get locked out constantly; often when in the middle of working on something. The plugin to “hide” the wp-admin directory doens’t work well, but has been tried to see if it would help as well (still got locked out then, too).
I’m have a VPS acount. I look at the raw acces logs in cpanel and never see any sort of major attack of wp-login.php. At most there’s 5 or 6 POST attempts and then you block… don’t you think it’s a bit too agressive to be locking out clients when there’s that few attempts? How about giving some leeway, eh? Especially for VPS accounts that are supposed to have dedicated resources so these attacks don’t impact anyone else on a shared server.
If you like, you may contact technical support in which they will be happy to remove the security measures that are locking you out. Of course, continue locking down your WordPress admin with a secondary password as well.
Thank you for replying. And, again, thanks for the article. 🙂
Couldn’t have been any simpler. Thanks
Hello, thanks for this article. I understand that wp-admin is actually a folder in WordPress, so if we add this code, won’t it lock down the whole directory and not just prevent people from accessing the wp-admin login page?
Thanks in advance for your advice.
The wp-admin directory only contains content that would be accessed on the admin dashboard so it would not affect the main content of your site at all.
Back in business!! Thanks to you and Jeff.
Regards,
Tony
That makes sense Jeff, I use WP as content management for this dynamic site so I tried
https://kissthesky.net/blog/wp-admin it then redirected to
https://kissthesky.net/blog/wp-login.php?redirect_to=http%3A%2F%2Fkissthesky.net%2Fblog%2Fwp-admin%2F&reauth=1
and displayed the same message ‘WordPress Login Temporarily Disabled’
Where to from here?
You need to lock down the blog itself within your .htaccess. So, you will need to place the .htaccess code within the .htaccess file that is located inside the blog directory. After 15 minutes, you will then be able to log in again.
Hello Tony,
I took a look at your login and it is appearing for me. It may have been blocked temporarily (typically 15 minutes) in order to stop brute force attacks. Make sure to review the article above for more information on how to secure your WordPress login.
By the way I was using the following URL: https://kissthesky.net/wp-admin
Make sure to clear your browser cache before trying to login again. Please let us know if you continue to have difficulty logging in.
Kindest regards,
Arnel C.
Jeff,
I was able to edit the file as you suggested but now when I attempt to log in using
https://kissthesky.net/wp-admin
I get the 404 error message.
This is because the website is not created using WordPress, so it will not contain a wp-admin directory.
Thanks Jeff!
Guess I’ll know in 15 minutes or so.
Hi Tony,
You might end up with a blank .htaccess file in WordPress if you haven’t yet gone to Settings/Permalinks and set and saved the permalink setting you want to use.
WordPress doesn’t generate the .htaccess info until you do that. If for some reason WordPress can’t write to the .htaccess file, you should get a notice warning you of that and also the code to copy and paste into your .htaccess file manually.
I have attempted to edit a client’s .htaccess file following instructions and the file is totally blank. There is no code to apply the Trusted Referrers fix to. Client’s url is
kissthesky.net
which is a addon domain to
stevesalmostfamous.com
Thanks in Advance
To apply this, you will need to copy the entire block of code mentioned into your .htaccess file and adjust it based on their specific information.
Just replace the login keyword with one of your choice and your website’s URL.
Hello Matt,
Sorry to hear that you’re having problems with the login. Since you did not give us any account information, we could not check into the matter for you. If you want us to investigate, please give us at least a domain name or account user name. If your site is being hit by the brute force attack, then you may not be able to access the admin until you implement one of the suggestions listed above (and then waiting 15 minutes).
Remember that posts here are public domain. If you would prefer the matter to be handled privately, then please contact our live support team as per the contact information at the bottom of the page.
Kindest regards,
Arnel C.
I’ve waited for 15 mins but still can’t log in. I’ll wait for half an hour and try again.
I have a number of WP sites which are in folders in my public_html folder. Each site is also running its WP from a folder. i.e. xyzxyz.com/qrgf/wp-admin/wp-login.php
I’d like to use the Referrer method above. What’s the best way?
Also, would it be preferable to put this in the .htaccess file that’s *above* my public_html folder? Could I put the Referrer for *all* of my sites there? (So they’d all be in one place)
You could simply place a single block of code within your .htaccess file in your public_html directory that covers all sites. As long as you don’t have any additional rules in deeper folders that could counteract it, everything can work directly within a single file. It would look something like this:
RewriteEngine on
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{HTTP_REFERER} !^https://(.*)?example\.com [NC]
RewriteCond %{HTTP_REFERER} !^https://(.*)?example\.com\/somethingelse [NC]
RewriteCond %{HTTP_REFERER} !^https://(.*)?example\.com\/anothersite [NC]
RewriteCond %{HTTP_REFERER} !^https://(.*)?example\.com\/additionalsite [NC]
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteRule ^(.*)$ – [F]
Be sure that you place each site that you are running in here or else you will get access denied errors on them.
I’m using the “Dynamic IP address access, limit by referer” method yet I am still getting block out of admin. This is the exact text in my .htaccess file:
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{HTTP_REFERER} !^https://(.*)?shadeofthebodhitree\.com [NC]
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteRule ^(.*)$ – [F]
</IfModule>
What am I doing wrong?
This disallows bots from sending direct POST requests to your WordPress admin, but if they are actively visiting your login page, they will still be able to launch brute force attacks. I recommend blocking based on IP, or using a secondary password here if you are still being locked out.
Help I have been locked out of my blog for several days and cannot reach my dashboard to make the changes suggested here. the site is
https://oakridgecameraclub.org/president/
any help would be appreciated. It appears I will need some help from the staff
Hello rob,
Sorry to hear about your troubles. As a test, I was able to access your admin login page using the Single IP method.
Make sure you are adding the code to your .htaccess file located in the root of your wordpress installation: public_html/president/
If you have any further questions, feel free to post them below.
Thank you,
-John-Paul
Unfortunately WooCommerce customers need to access wp-admin.php for some reason so an additional username and password won’t work for me. In fact whenever these blocks happed I think my customers are locked out from completing purchases. I guess they’ll just go elsewhere.
Instead of locking down with a secondard password, you could lock down your WordPress admin by referrer (under the heading “Dynamic IP address access, limit by referer”) which would prevent users from directly sending POST requests and allowing your users to still access their accounts.
Your instructions, above, are flawed.
They read:
To allow access from a single IP address, replace 123\.123\.123\.123 with your own IP address
But that’s not correct. You can’t simply plug in “your own IP address”—you also have to insert slashes.
It should work in most cases either way you type in your IP address:
Both methods of typing in an IP address should be valid for an .htaccess file.
I see from you account notes that you might have also had an extra space throwing the rules off. Thanks for leaving this comment. I’ll see about updating the article to make it a little more clear how to enter in your IP address, but I’m also almost done working on a WordPress plugin that will allow our customers to easily implement these security recommendations on their own automatically without issues.
Thanks again, and please let us know if you had any other suggestions!
– Jacob
Hello suryandh,
To map your WordPress admin to a subdomain insead of being at /wp-admin, you would use the folloeing within your .htaccess file:
# Redirect sub folders to sub domains
RedirectMatch 301 ^/wp-admin/?(.*)$ https://admin.domain.com/$1
Of course, modify the domain to what you will be using within your site. You will also need that subdomain set up within your account there as well.
I have a problem….. plz tell me htaccess rule to set up a wodpress management server to a subdomain like admin.subdomain.com . And URL should be stored in database(RDS Mysql server)i am using aws server and cloudfront DNS ,CDN,WP super cache plugin to access wp-content by n wordpress servers…… Plz mail me asa fast as possible……..
The reason that you may not get this error when the installation is in another directory is because the bots may not be targeting the subdirectory at this time. It is possible that this can indeed happen to sites on those directories as well, so it is best to still set a secondary password within your .htaccess file.
Hello jkwalz108,
The fix you are using is for when “the brute force attack that is taking place relies on sending direct POST requests right to your wp-login.php script,” but if your site is accessed directly, then the wp-admin is requested it will still allow attempts through.
A better option for you would be to use a “Secondary WordPress admin .htaccess password (Recommended if your IP changes)”, or the Multiple IP addresses” method.
If you have any further questions, feel free to post them below.
Thank you,
-John-Paul
I have implemented the “Multiple IP address access” method on all my domains yet I am still getting locked out of my admin. Does this method no longer work? Here is the exact text I have at the head of the .htaccess file:
RewriteEngine on
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{HTTP_REFERER} !^https://(.*)?shadeofthebodhitree\.com [NC]
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteRule ^(.*)$ – [F]
Typically we wouldn’t recommend turning off ModSec as it will protect your website from other attacks and not just the WordPress brute force ones. It’s kind of a last resort if you really need to get back in to your WordPress admin dashboard and have been having issues with our ModSecurity rules continuing to trigger.
If you wanted to test the limit by referer method in your .htaccess file, you would need to create an HTML form with the method set to POST and the action set to your wp-login.php file of your website.
It would look something like this:
You would get a 403 forbidden error if the .htaccess rules were applied correctly. You could then hit refresh on the page and it should show your normal wp-login.php page, as you would only be restricting POST attempts to the page, and when you hit refresh that is simply a GET request.
We also actually recommend setting up a secondary WordPress .htaccess password for the best level of protection.
Please let us know if you had any further questions.
– Jacob
Hi,
I just implemented the “limit by referer” method in my .htaccess file, but before I turn off Modsec, I want to be sure my implementation works. How can I test this?
Furthermore, I noticed that this solution only promises to address the current botnet, which uses direct POST requests. Is there any way we can be prepared for future modes of attack, or is this a watertight solution for any eventuality?
Using the IP address restricting method that is discussed in this article is best suited for when you have the same IP address consistently, or at least rotate through a few common ones.
Being that it sounds like you’d be accessing your WordPress admin dashboard from more than likely dynamic IP addresses, while you could keep figuring out your IP address by using our IP lookup tool and updating your .htaccess rules to let the new IP in. You will probably find it much easier to instead prevent WordPress login attempts with a .htaccess password.
That way you’d simply enter the username and password you set, and then no matter what your IP is it will bypass the .htaccess block, and give you the normal WordPress admin dashboard login.
I went ahead and set this up for you to speed up the process, and all you’d have to do now is just open up your /public_html/.htaccess file and you should see I left you a note at the top with what I set the username and password to. If you’d like to use different credentials, then you can simply follow the steps in that other article and create an additional user.
I hope that helps you out, and please let us know if you had any other questions at all!
– Jacob
I was wondering how the ip address lock down affects me using my iphone wordpress app, or using my laptop to login from a library? Is there a way to find out my iphone ip address? does this change depending on who’s wifi Im using? Are there any other security measures I could take ?
Hello again Kdemerly2!
The options above are widely considered to be viable options to helping to lockdown your WordPress login. If you are using the referrer method (which is what I saw in your .htaccess file), then you should make sure that you login using the url like this: https://jeffchoirs.org/wp-admin . The referrer method of blocking is used because the automated scripts in many of the attacks are using the direct path to the login page.
The script used in the attacks will not normally use a the domain name, but it can happen which may be why you’re seeing your page often blocked. I would highly recommend the IP method if it continues to be an issue. This would prevent you from continually being blocked by simply typing in your site URL. I understand how frustrating this can be trying to get into the WordPress page – hopefully, using the IP method will keep you safer.
Using Cloudflare is a viable option if you wish. It adds a little complexity to the setup, but they are free and they offer other services which may be helpful to you. We also have documentation for the setup here: Cloudflare setup.
If you continue to have any problems, please let us know if you require further assistance.
Regards,
Arnel C.
Hello Mcsiler,
I’m sorry for the frustrations that you’ve been having with your WordPress site. One of our Tier2c techs (Shawn C.) has been looking at it and finally cracked the issue. The problem was with your caching plugin. It needed to be cleared as it was basically causing the connection issues for the database. Once that was done, the page came up beautifully.
If you ever need to disable plugins, there’s a guide we provide that can help you do it real quick so that you can eliminate/identify them as the possible cause for your WordPress problems: Disabling WordPress plugins. Otherwise, please let us know if we can help by posting another question!
Thanks for your patience! Regards,
Arnel C.
Hello Kdemerly2,
The “” is required in order to recognize the period in between the domain name and it’s extension. Iso the 404 for the the link you provided. The problem is that the page does NOT exist. So if you’re typing it in directly, there’s no such folder in your directory. If you’re getting a 404 elsewhere, I need to see the URL for it. WordPress generates the URLs for pages that are in it – they will not be the same as the title of a page that you may have created directly in WordPress. You can create custom permalinks, using the permalinks option in WordPress, but you can’t simply create a url for a single page. I hope that helps to explain it. The URL that you provided indicates that there should be a subdomain/folder named “varsity-singers” and there isn’t one. That’s the reason you’re getting the error message. Create one, add some website files in there, and you’ll see it appear with no problem.
I hope that helps to clear up that issue! Let us know if you’re still having any specific problems.
Regards,
Arnel C.
Thanks for your help. I appreciate it.
So should I try and limit the login again, using the steps above? I guess I can try.
And after waiting, I can now log back in to my WordPress site. So, while I was happy to lock it down using the steps listed above, it did not seem to work for me. I can certainly utilize Cloudflare if that’s a viable option.
When I go to that page https://jeffchoirs.org/varsity-singers.html/
I get: “This is somewhat embarrassing, isn’t it? It seems we can’t find what you’re looking for. Perhaps searching, or one of the links below, can help.” I don’t know where the disconnect is, but my WordPress page for Varsity Singers isn’t jeffchoirs.org/varsity-singers.html/.
Hello Kdemerly2,
The way you put the link in won’t be recognized correctly. Try this:
https://jeffchoirs.org/varsity-singers.html/
You’ll see it everytime that way. When you leave off the “.html” server is looking for a subdomain or folder that does not exist. When I looked for that, I did not see, so that’s why I thought there was no such location. The link works from WordPress most likely because it’s linked TO the .html page. Anyways, if you’re going to go directly to an html page in your directory, then you would need to provide the extension in the URL.
Regards,
Arnel C.
The page exists! It was there until I put in your code. If you go to that page again, you’ll see that it works now – because I removed your code and put back what was in there a few hours ago before I tried this update. https://jeffchoirs.org/varsity-singers/ But now I’m locked out of the login again. *sigh*
I had that backslash in there originally, and it still prevented me from even accessing my pages outside of logging in. That’s when I tried removing it, thinking maybe it was the cause. Isn’t that just supposed to prevent login issues? Why can’t I get to https://jeffchoirs.org/varsity-singers/ without logging in? Why do I get a 404 error when I’m not even logging in to that page? Thanks for your prompt response, btw!
I’m STILL having issues – no website at all and cannot even access the dashboard on wordpress! longbeachlpa.com. Apparently someone is working on it, but I have never ever had these issues with any website until this year on Inmotion – getting very very frustrated.
Hello Kdemerly2,
Sorry to hear about the problem you were having. Thank you for providing a link so that I could find the account immediately! I looked at the .htaccess file that you edited and you missed one little backslash that’s supposed to go before the period in ‘.org’. I went ahead and fixed it for you. Give it another 15-20 minutes, and then try to login again.
Apologies again for the issues – hope this fixes it for you!
Regards,
Arnel C.
I followed the steps (using the referrer method), and now not only can I not log in, all of my pages (excpet the homepage) are showing 404 errors – even when I’m just browsing the site. https://jeffchoirs.org/
Hello Mcsiler,
I’m sorry to hear you are having problems with the admin login. Unfortunately, this issue isn’t something that just simply goes away and never comes back. If your website was specifically targeted, then the botnet may subside for a bit, and then come back later with more attempts to hack your login. The lockout doesn’t mean your website is “hacked”. It means that an attempt to attack your site was stopped and the lockout occurs because of failed attempts to login to your WordPress admin. Please allow the time for the lockout to pass (15 minutes) and then try to log in again.
If you continue to have login problems, please either contact our live technical support staff, or provide us more information on the URL you’re having the problem with so that we can investigate the issue in more depth.
Kindest regards,
Arnel C.
This has happened COUNTLESS TIMES and it gets me in, but then a few days later it is supposedly hacked again. This does not happen to ANY of my other sites, just one.
Hello Camhawk,
I was trying to say use the “https://example.com/wp-admin” path so that the referrer rule in .htaccess recognizes it as a legitimate access to the Administrator dashboard.
When you implement the .htaccess rule, you should give it at least 15-20 minutes before trying to access it again. As per step 9 above: “Unfortunately even if you simply try to access the WordPress admin dashboard, still within the 15 minute window of a block, this could extend the block an additional 15 minutes, so it’s important to wait for the previous block to expire before attempting to access your WordPress site again.”
After you’ve waited, make sure that access to the Administrator dashboard is occurring through the link using “http;//example.com/wp-admin” (but “example.com is replaced by your name). If the problem with the login continues, then you may need to use the multiple IP option.
Please let us know if the issue persists and we can investigate it further.
Regards,
Arnel C.
Thanks, but I seem to be struggling with your explanation.
– When you say “Give your members a URL shortcut using the domain URL” do you mean create a URL like this (https://www.example.com/login) when linking to the login page and have it NOT redirect to the wp-login.php, i.e. so it stays on /login
I have done the above without using .htaccess, but when I add the .htaccess referrer rules it starts redirecting my /login page to wp-login.php and eventually locks me out again.
Any further help much appreciated.
Hello Camhawk,
Thanks for the question! If you have many members logging in and you would prefer not to limit by the IP address (IP address would be unique per user), then you should be using the Referrer method as listed above. Give your members a URL shortcut using the domain URL. The default reference to login for the WordPress admin is as follows: https://domain_name.com/wp-admin. This way you’re not using the direct login to wp-login.php (it automatically redirects to the wp-login using the wp-admin, anyway) and you’re using the URL as per the .htaccess rule.
I hope that helps to clarify the matter. If you require any further assistance, please let us know.
Regards,
Arnel C.
Hi,
My members use wp-login.php to access their accounts. How do I accommodate them using the above solution?
Cheers
Sorry, please disregard my post. I am at wrong page.
When I use the following .htaccess file on the subdomain(test.mydomain.com), I get the error “310 (net::ERR_TOO_MANY_REDIRECTS)” and can’t access the log-in page.
AuthName “Login”
AuthType Basic
AuthUserFile /home/xxxx/.htpasswd
require valid-user
Although I have tested on the local using XAMPP creating subdomain “test.localhost” and subdirectory on the inmotion server “mydomain.com/test/ ” with same files and it works fine.
Why am I getting the error only on subdomain settings?
I am working on a script that will use 2 htacces files. If the visit to a site exceeds a certain expected number per 10min, the htacces file will be changed on the fly for an hour. The changed file will limit access to where most expected visitors will com from. For instance your own country. This will also prevent brute force attacs from a large amount of computers, and keep open your site to mayby 95% of your users depending on what kind of site it is. It should be possible to customize the ‘access denied’ page on the fly also to inform, in case you have your own server.
It is the order of Allow, Deny that determines weather it works or not.
This does not work:
[code]
Order Allow,Deny
Allow from 111.93.52.182
Deny from all
[/code]
Because it first allows from 111.93.52.182 and then denies from all.
This works:
[code]
Order Deny, Allow
Allow from 111.93.52.182
Deny from all
[/code]
Because you first denies from all and then allows from specific.
Which of the 2 lines that comes first is not important. Only the Order line.
Hello andyks,
Thank you for your question. I tested this, and it works when you comment our the line:
Deny from all
For example:
[code]
Order Allow,Deny
Allow from 111.93.52.182
#Deny from all
Also, as suggested in this guide, I added it to the top of the .htaccess file.
If you have any further questions, feel free to post them below.
Thank you,
-John-Paul
Hi, my IP address 111.93.52.182 and I used this code in .htaccess of my wordpress blog Sharecommons.com:
[code]
Order Allow,Deny
Allow from 111.93.52.182
Deny from all
Well, it is supposed to allow me and deny all other IP addresses. However, it has locked me out and is blocking me from accessing the wp-login.php page. What could I possibly be doing wrong here? Thanks for your help.