There has been an increasing trend of brute force attacks on WordPress websites, and we recommend following the steps in our WordPress wp-login.php brute force attack news update for steps to take to lock down and secure your WordPress installation.
Why is WordPress targeted?
WordPress is one of the one most widely used website solutions on the internet today. As a result, it is also very often the target of malicious activity. Recently, there has been a trend in increased brute force attacks aiming to get access to WordPress as administrator-level users. This is in part due to the nature of WordPress and how it evolved into the website solution it is today. WordPress was originally designed to be simple blogging software. However, it is often used for many other purposes such as eCommerce, bulletin boards, personal journals, etc. This makes these websites more valuable as targets. Hackers often want to either disrupt this traffic or to somehow obtain information from these websites.
What is a Brute Force Attack?
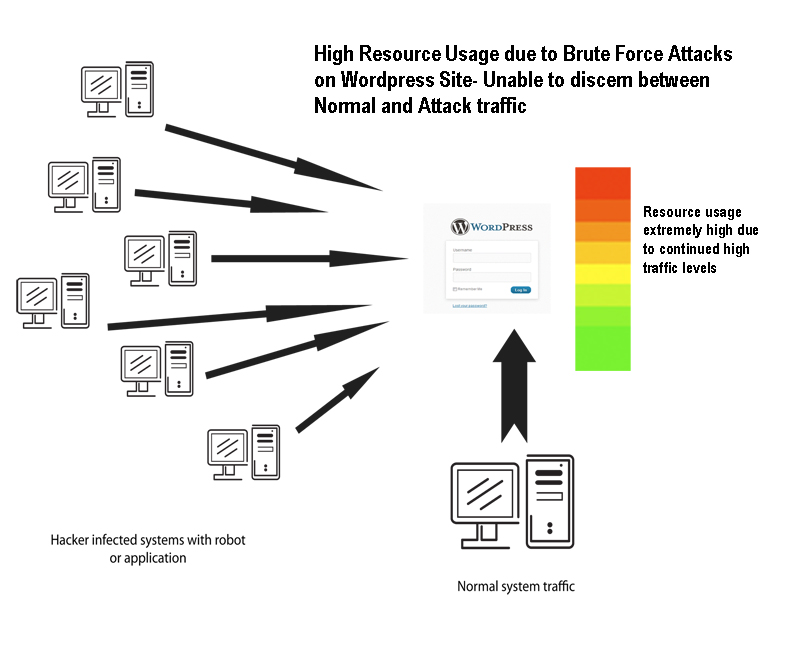
One of the methods to gain information -primarily LOG-IN information – is by using a method called BRUTE FORCE attack. Basically, as the name suggests, they are not hiding the attack, and there’s no efficiency to the attack. You could say it’s like taking the “shotgun approach.” It simply is hitting the server looking for one thing, the correct login information for your WordPress site. Hackers will often infect other computer systems and then set them to attempt logging into the WordPress Administrator. The illustration below shows graphically how the attack traffic can come from many locations and be mixed with normal website traffic. The attack can also come from just one location, but the method of trying to crack the login is the same – it is simply going through a sequential search for your login. Brute force attacks can also increase resource usage of the website. Therefore, brute force attacks are not only trying to crack through your security, but they are also driving up resource usage when multiple attempts on the WordPress login is occurring.
Preventing WordPress Brute Force Attacks
Since users are no longer using WordPress as simply a blogging solution, there isn’t as much emphasis on user management for the owners of the WordPress site. And this may also be a contributing factor to the problem. WordPress Site Administrators should regularly cycle their passwords and review their user lists to make sure that no one has been added that isn’t supposed to be on the list. Especially users added as Administrator-level users. There are also WordPress sites that do not require that people register to post comments or other actions on the website. To prevent unauthorized access we recommend the following:
- Block access to the WP-LOGIN.PHP using the HTACCESS file by requiring an additional password
- Block access to the WP-LOGIN.PHP using the HTACCESS file by allowing only a specific IP address or range of IP addresses
- Find a plugin that prevents access to the login screen after a particular number of tries. The plugin should then use an interval of inaccessibility before the next attempt to log in would be allowed.
The first two methods using .htaccess are recommended as they will help to prevent excessive resource usage. There is no guarantee of this with the plug-in unless the plugin can limit access no matter how many times login attempts are being made. The following information are examples of the code solutions for the .htaccess file as listed above
.HTACCESS method to deny user login using an additional password for wp-login access:
Note: The code below would be in the .htaccess file located in the .htaccess file located where you have installed WordPress
AuthName “WordPress”
AuthType Basic
AuthUserFile /home/username/.htpasswd
Require valid-user
</FilesMatch>
.HTACCESS method to deny user login using a specific IP address or range of IP addresses:
Note: The below code needs to be in the .htaccess file located in the WP-ADMIN folder. If you don’t see one, then create a blank text file and name it .htaccess saving it in the wp-admin folder
AuthUserFile /dev/null
AuthGroupFile /dev/null
AuthName “Admin Access Only”
AuthType Basic
<LIMIT GET>
order deny,allow
deny from all
# whitelist Admin 1 IP address
allow from xx.xx.xx.xxx
# whitelist Admin 2 IP address
allow from xx.xx.xx.xxx
</LIMIT>
